Context
Risks from third parties
- 80% of companies have suffered a breach due to a third party
- 77% of companies say they have limited visibility into third-party vendors – Source S&P Global 2022
- More than half of organizations (51%) have suffered a data breach caused by a third party – Pool SOUCE Ponemon
- According to Forrester, il 60% of security incidents in 2023 will derive from problems with third parties – Source Forrester
RISK(OUT) SAFET(IN)
MEASURE, MONITOR AND REDUCE THIRD PARTY RISK BY ALIGNING IT WITH ORGANIZATIONAL GOALS.
Increase your confidence level thanks to riskout! Reach your goals every day with:
Assessment
The assessment of the level of criticality of new and existing suppliers
Monitoring
Continuous risk monitoring of the supplier base
Analyses
The comparative analysis of the security posture of third parties
WITH RISKOUT
Build a highly performing and automated third party risk management program

Evaluate suppliers based on their scope of supply, the type of data processed and according to standards and best practices

Customize controls according to the type of market you belong to

Define the acceptable level of risk for your organization

Analyze and manage the risk of each supplier and the general risk in real time

Compare the performance of suppliers with each other

It governs the life cycle of each third party in the information & cyber security field

Elevate your organization's resilience by managing the risk of your most exposed perimeter
Main features


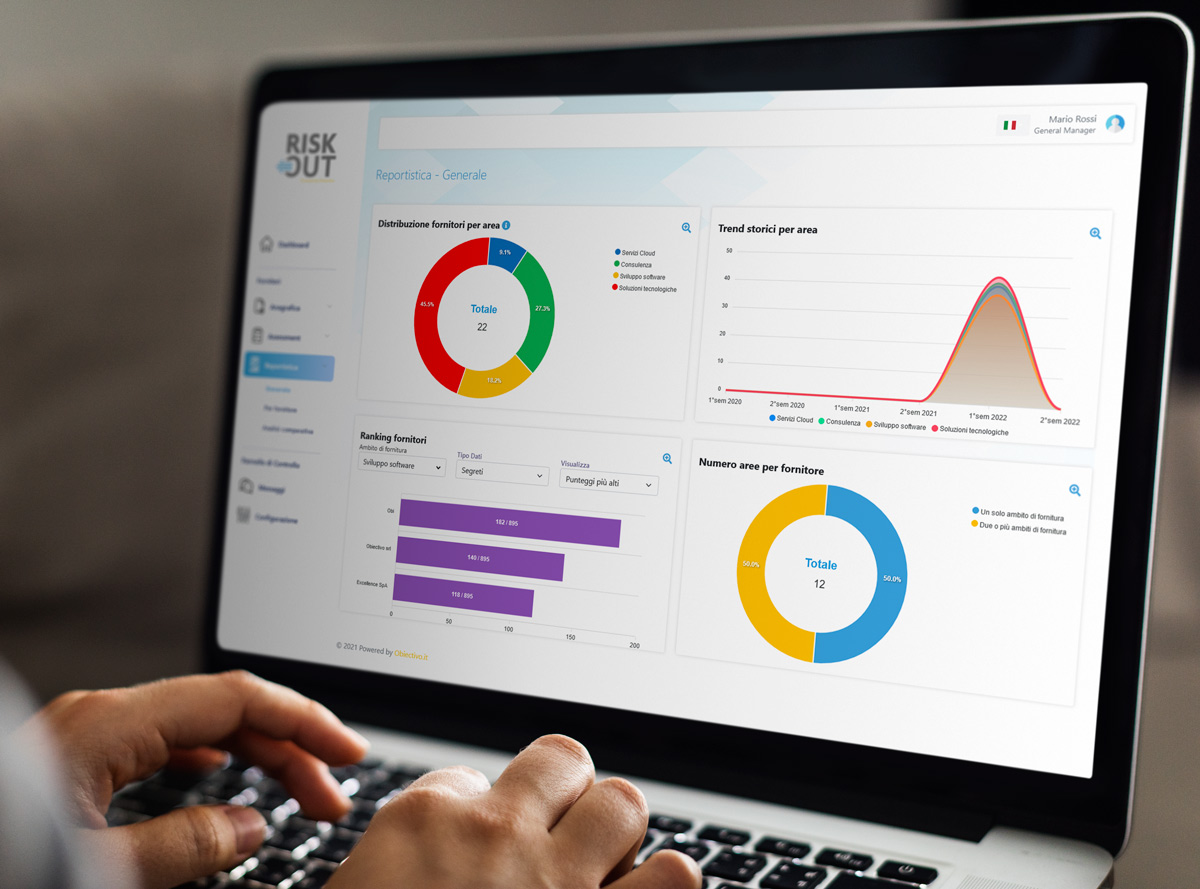
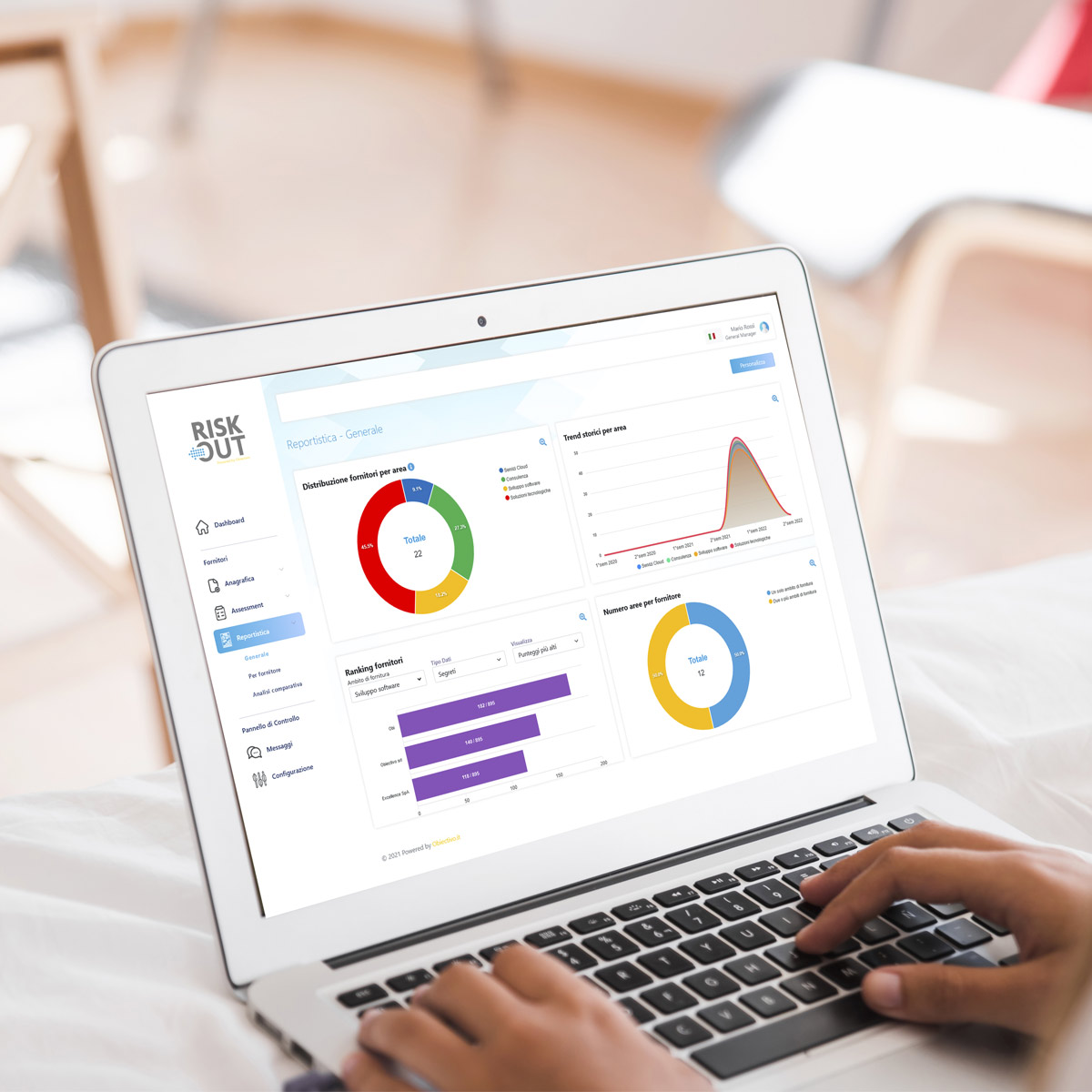
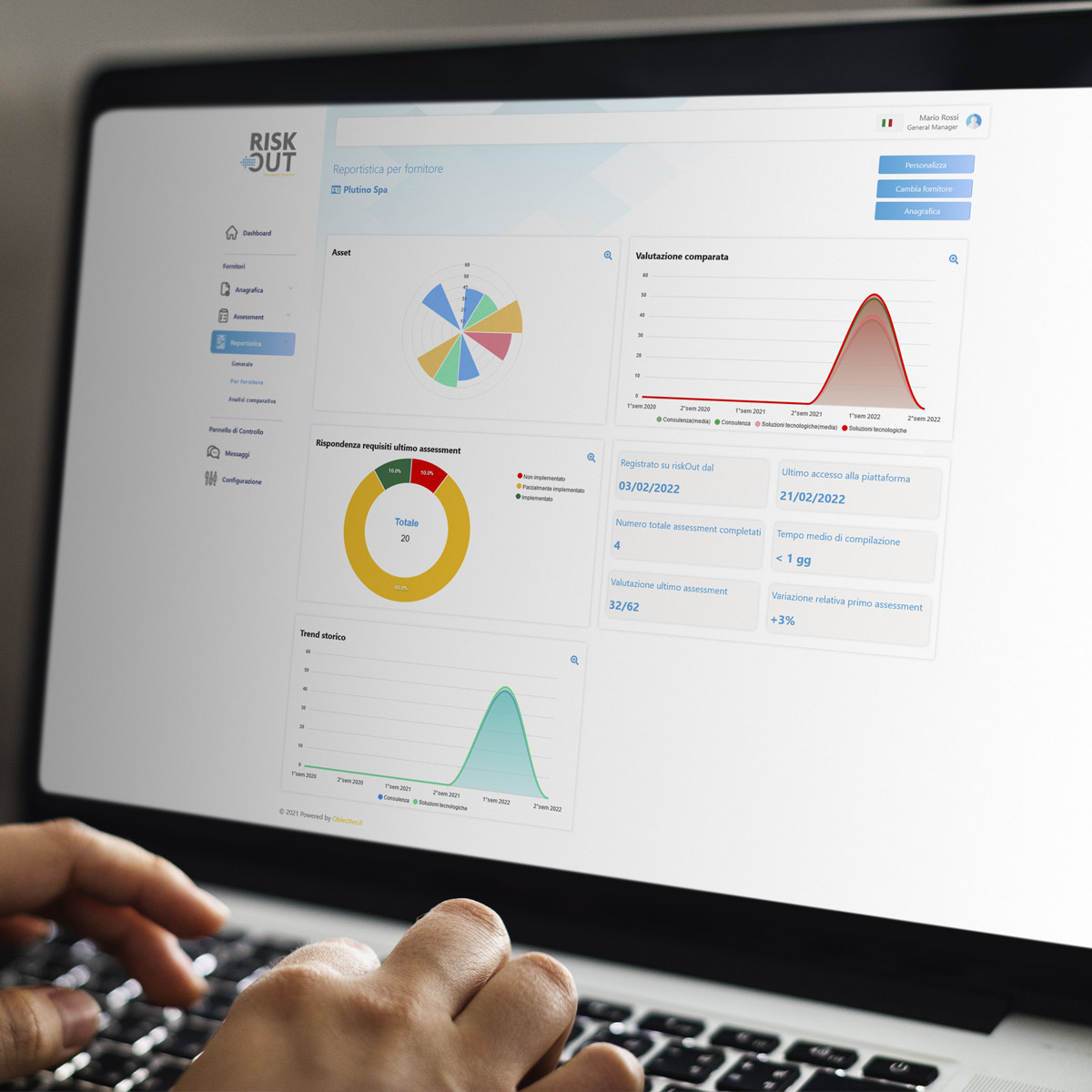
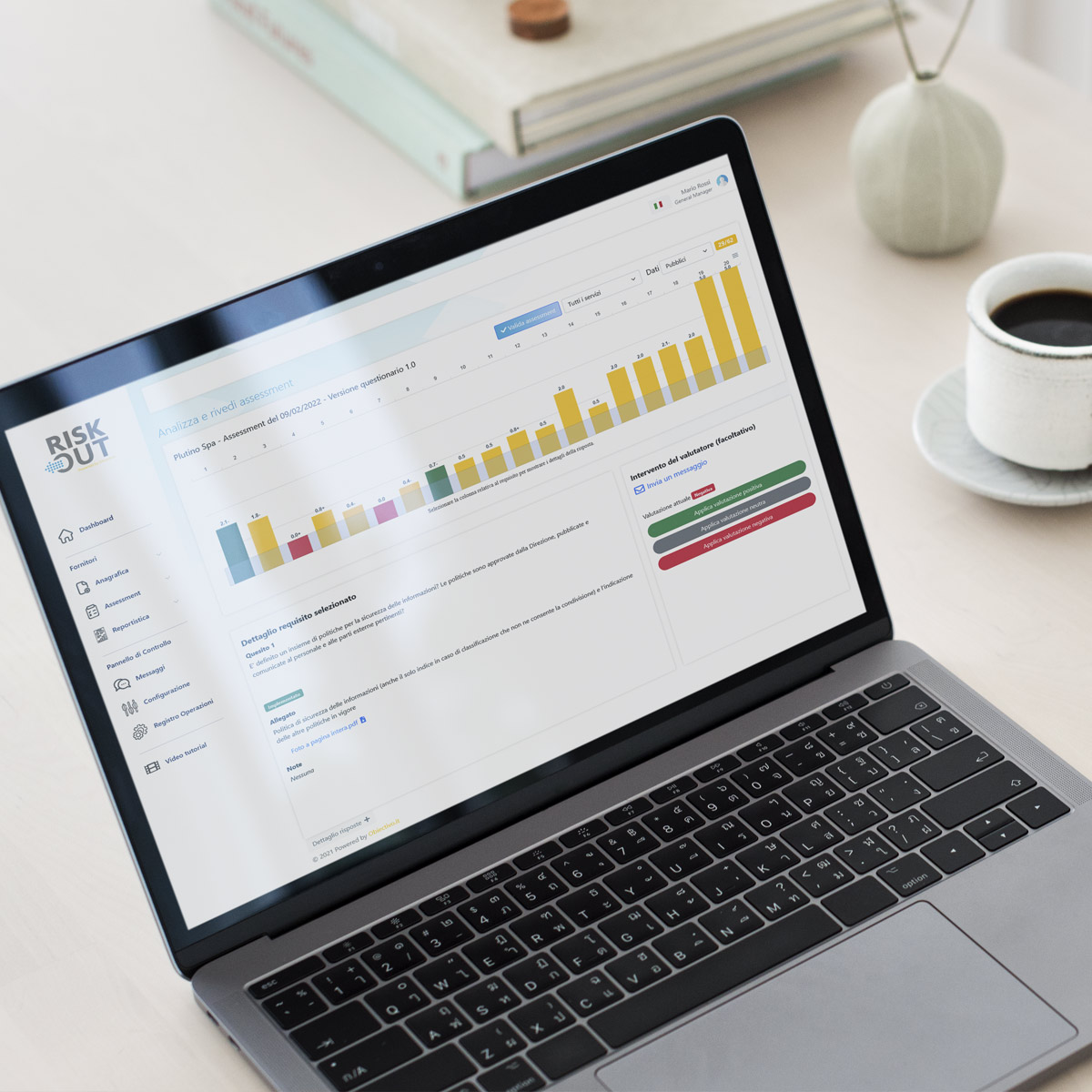


The benefits of our platform
Get confident in your program
Structured data, real-time reports, adherence to standards and the possibility of carrying out audits make it possible to obtain reliable surveys and evaluations
Drive efficiency and reduce costs
Reduce operational costs through automated processes saving time and resources
A single method of risk assessment
Analyze and evaluate the risk of your suppliers in a standardized and centralized way
Improve decision-making process and level of compliance
Consistent data allow the implementation of the most appropriate mitigation strategies and adherence to policies
